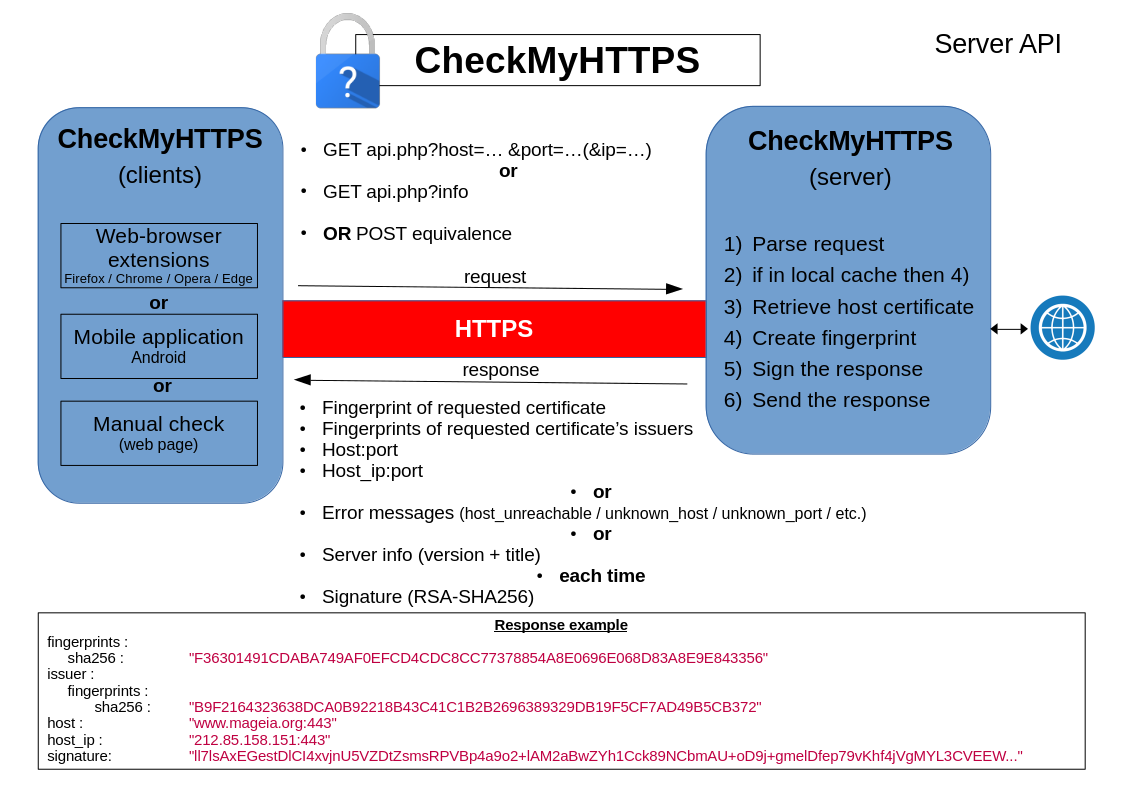
Explanations
CheckmyHTTPS verifies that the certificate you receive is the one issued by the server you are visiting. It works as shown in the following diagram:
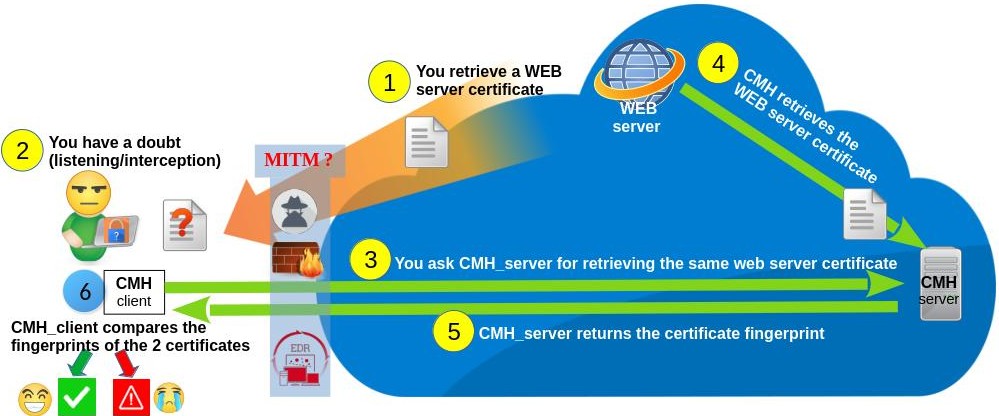
* The check server is 'checkmyhttps.net' by default. You can replace it with your own (see GitHub).
We have developed several clients that use this method (web browser extensions, mobile applications, test web pages). These clients interact with the verification server via an API (Application Programming Interface) as follows :